Google SSL changes that could affect your website's trust
- Details
- Category: Latest News
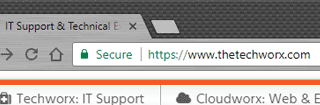
On October 27th, a new version of Google Chrome will be released that will prominently label any site without an SSL Certificate as “non-secure” in the browser bar.
Your website will be affected by this change if it is not loaded over https://, contains input fields, asks for passwords or any other sensitive data, or is visited in incognito mode.
Read more: Google SSL changes that could affect your website's trust




 We can repair and replace failed/broken hardware components and screens on most laptops and notebooks inc. Apple MacBook's.
We can repair and replace failed/broken hardware components and screens on most laptops and notebooks inc. Apple MacBook's.  We offer free local call-out & diagnosis to all our clients and fixed price quotes - In the unlikely event we can't
We offer free local call-out & diagnosis to all our clients and fixed price quotes - In the unlikely event we can't We treat our home and business clients in exactly the same way, delivering a friendly, professional service to the very
We treat our home and business clients in exactly the same way, delivering a friendly, professional service to the very Whether in your office or on the go, you get cloud email, document storage and Office applications - always the latest
Whether in your office or on the go, you get cloud email, document storage and Office applications - always the latest Personal blogs, Micro Business-Card Websites or large CMS/eCommerce sites. We can design and develop the perfect site for you or
Personal blogs, Micro Business-Card Websites or large CMS/eCommerce sites. We can design and develop the perfect site for you or